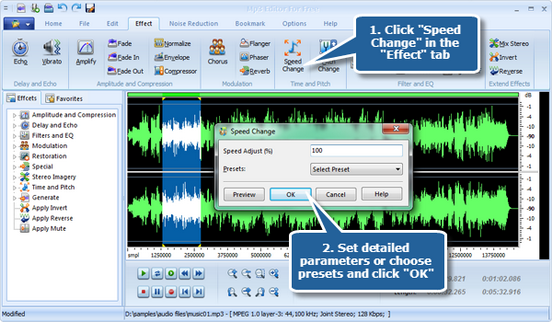
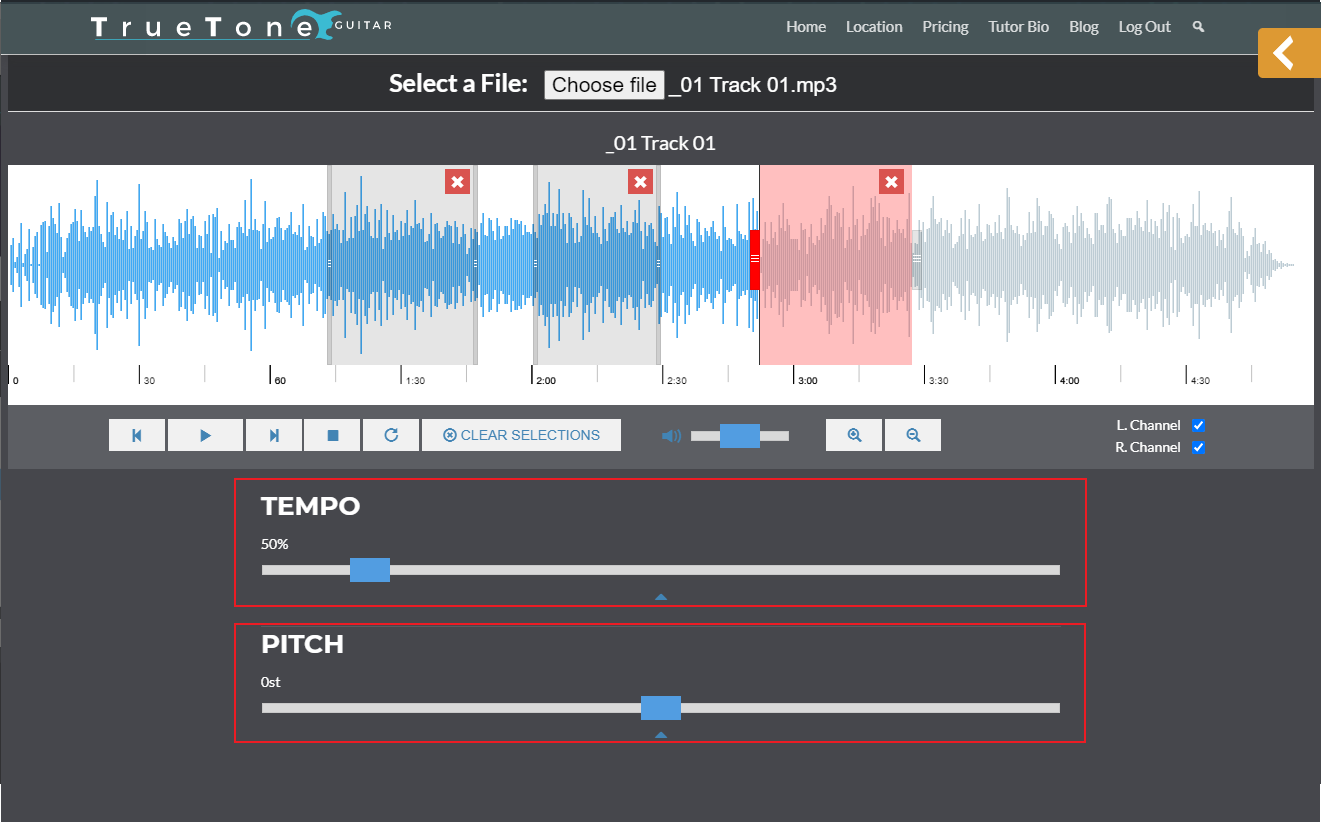
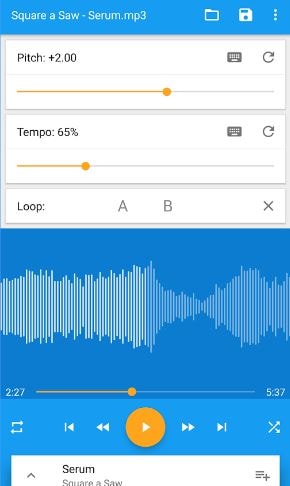
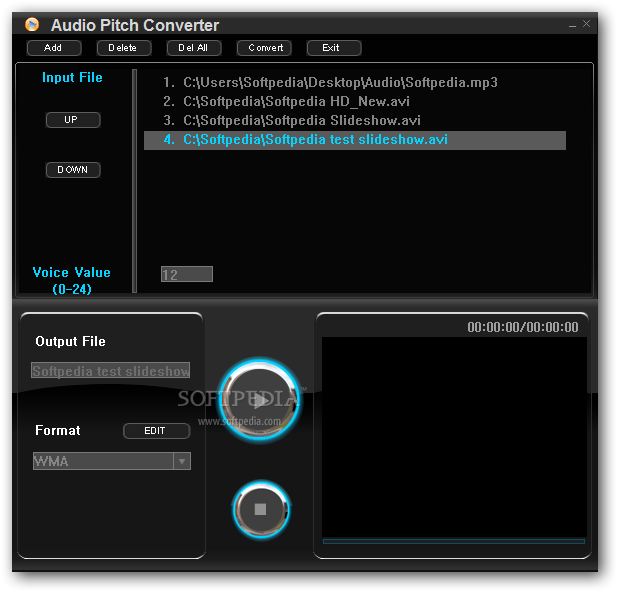
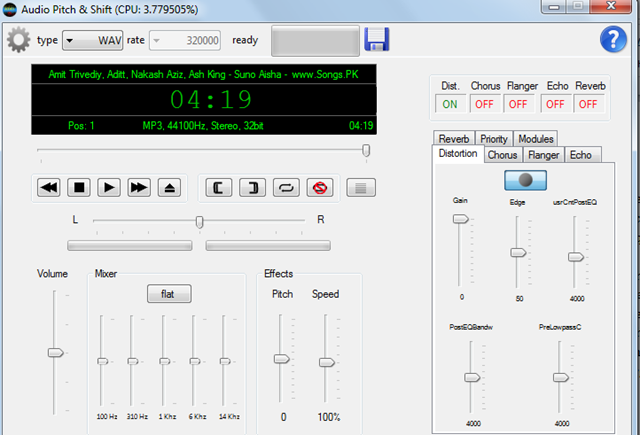
How to Instantly Transpose Any Audio File into a Different Key for Free! Change Pitch in Audacity - YouTube

Amazon.com: Studebaker 3-Speed Pitch Control Turntable with Bluetooth Receiver AM/FM Stereo Radio/USB Slot for MP3 Playback/Headphone and Aux in Jacks (Teal) : Electronics